Exposure Management Platform
Hyperconverged security for your entire network, infrastructure, and devices.
Request a Demo
The only platform with complete visibility
At UncommonX, our agentless, fact-based discovery is the cornerstone of our AI-powered Exposure Management Platform. It delivers unparalleled visibility and control over your entire network without the need for intrusive software agents. Our platform offers the only evidenced based single pane of glass for all network, security, and connected IT, OT, and IoT assets and the insight to prioritize the most important items needed to protect your organization.
Learn more about Exposure Management →

AI-driven by design
Our platform turns raw data into real-time risk insights, automating discovery, enhancing context, and empowering secure decisions with precision and speed.
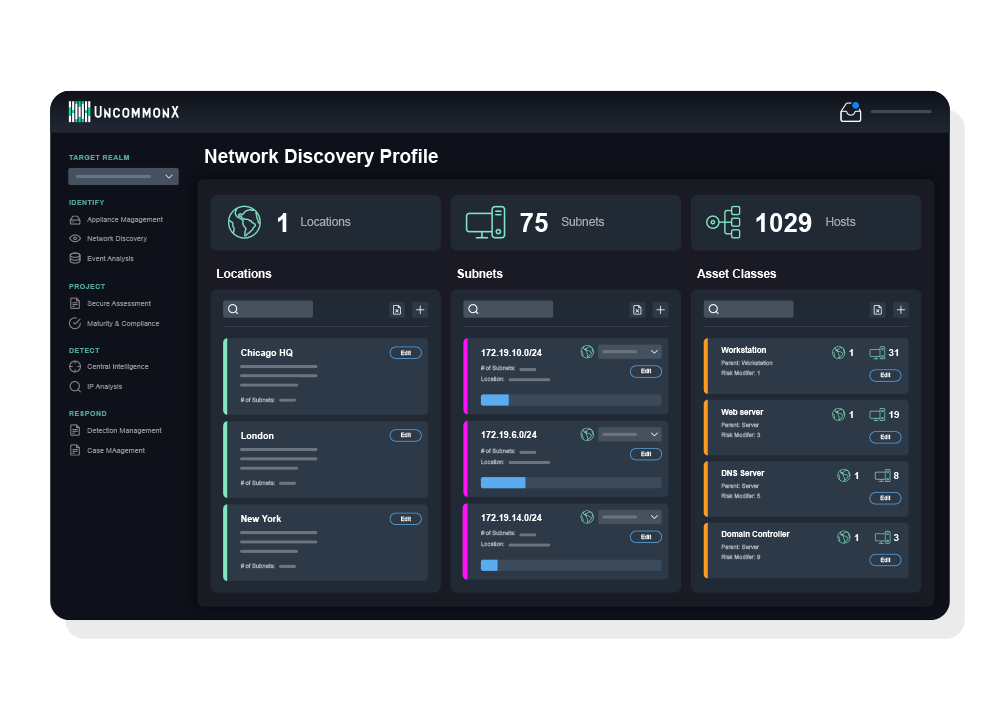
Intelligent profiling
Patented discovery and visibility
At the core of our platform is a powerful AI engine that discovers network data, asset behaviors, and threat intelligence to improve security outcomes. AI fingerprinting automates the identification, classification, and profiling of devices to build a complete and current view of your environment.
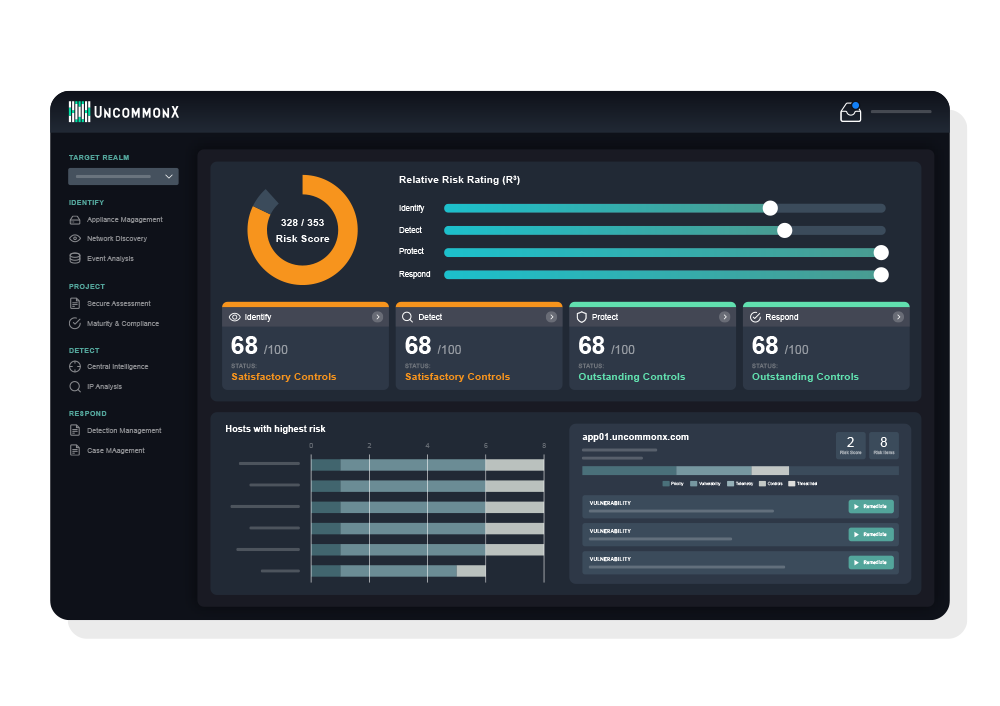
Relative risk
Personalized scoring that adapts
UncommonX AI enhances our patented R3 scoring model by factoring in real-world context unique to your organization. It learns from system changes, usage patterns, and threat updates to produce more accurate risk insights that help your team focus on what matters most.
Real-time context
Explicit actions, optimized results
Our technology uses AI to assess real-time context and recommend the most important actions based on system data and LLMs. It provides explicit instructions to automate remediation, enhance security, and reduce spend. Proactive and preemptive security.
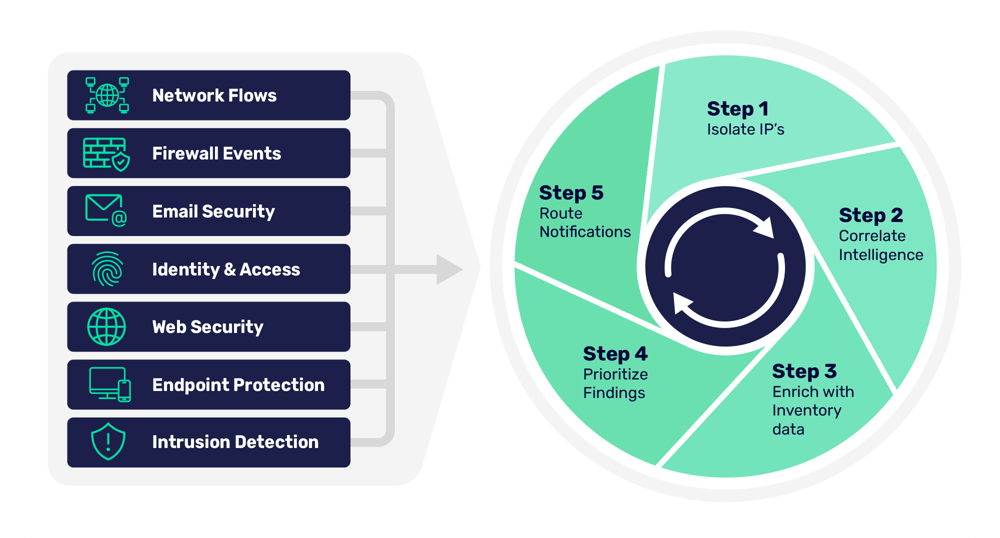
How it works
Agentless technology seamlessly integrates with hundreds of common IT products, regardless of brand, to analyze, prioritize, and deliver real-time data on network risks and threats. The system provides explicit actions to automated tools, teams, or individuals to reduce risk and build long-term resiliency.
Go agentless
Monitor all devices and connections without messy agents, using network protocols, APIs, and passive methods like NetFlow. Provide a comprehensive view of IT, OT, and IoT devices, delivering an accurate, real-time inventory.
Learn more about Agentless Discovery →
Integrate everything
Leverage universal integration capabilities agnostic of security brand from initial install. This seamless process offers “out of the box” connections to 100s of common IT products, from firewalls to OT to Cloud applications.

Rate risk in real time
See real-time visualization and reporting all in one place. This "single pane of glass" delivers deep and intelligent insight into any environment to compare risk readiness scores to industry norms, and the best way to optimize IT resources.
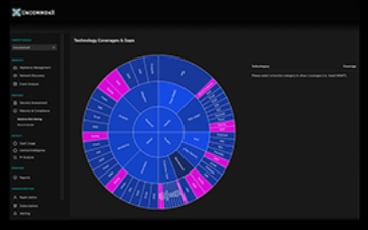
Map vulnerabilities to the NIST framework, highlighting high-priority issues and opportunities for improvement.
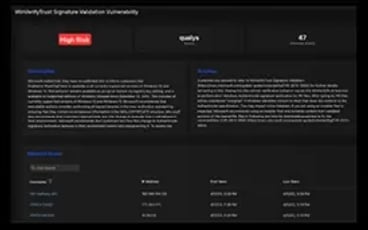
Generate a report of all hosts with specific vulnerabilities, then assign and manage them through remediation workflows.
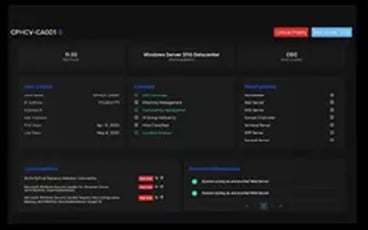
Devices with designated priority will score higher risk under specified conditions compared to standard assets.
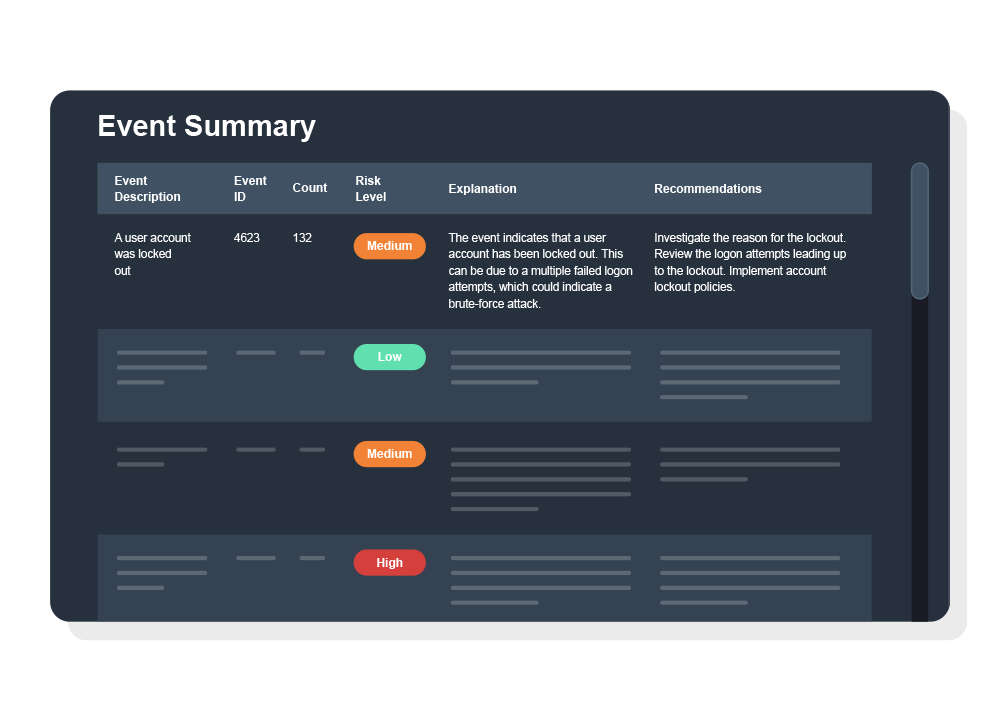
Manage every event
Collect, aggregate, and analyze data from across modern network environments. Our platform acts as a SIEM, providing an elevated level of visibility and analysis not found in typical systems, and offering secure storage for ongoing analysis.


Address threats, fast
Our platform combines multiple threat feeds, including our proprietary intelligence refined over a decade, to analyze event streams and correlate them with threat data, delivering confidence metrics, so you can take swift preventative action.
Detect and Respond
UncommonX’s detection and response process aggregates and analyzes data from a wide range of sources, including IoT, OT, and traditional IT devices. By leveraging advanced AI and data analysis, we correlate context to identify what is ‘normal’ in your network and sift through alerts and anomalies, focusing on those with the highest threat level or risk. Our system continuously refines itself, applying insights from previous incidents to improve detection and response.
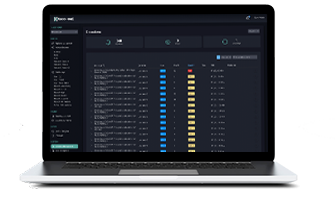
Proven, patented technology
UncommonX’s patented Technology Workflow aggregates and analyzes data from a wide range of sources, including IoT, OT, and traditional IT devices and works alongside your existing security tools. When we say patented, we mean it. Twenty-four patents and counting. All recognized for innovations in Exposure Management and AI, providing our customers with complete visibility of their entire networks and their relative risk in real time.
.png?width=179&height=250&name=patents-badge-blue%20(1).png)
Request a platform demo
Learn more about Exposure Management and how our patented platform can help your business achieve complete visibility and 24/7 protection across your entire network.
Technology insights
Read more about gaining complete visibility in our blog
Combating Rising Data Breach Costs With an Exposure Management Partner
A 24/7 SOC is critical for maintaining a strong cybersecurity posture. Employing one through an MSP partner delivers operational efficiencies and ROI.
Read Blog
Agent vs Agentless: Unifying Asset Discovery Under One Platform
Learn about the differences between agent-based and agentless solutions, as well as the often misunderstood role “sensors” play in agent-based discovery.
Read Blog
Combating Third-Party Domain Spoofing
Learn how organizations are currently addressing spoofing, and a new approach IT and cybersecurity teams should consider as part of their larger cyber resilience programs.
Watch Now

