Complete visibility,
hyperconverged cybersecurity
The only Exposure Management Platform you’ll ever need
Request a Demo
Why UncommonX
Complex digital environments with on-prem, cloud, mobile, and SaaS apps are forcing IT teams to manage too many tools, increasing costs without improving security outcomes. Our patented AI-powered Exposure Management platform sees everything, secures it, and saves you money.

See everything
Unprecedented network visibility
Our agentless discovery technology gives you complete visibility across on-prem, cloud, and connected assets—without intrusive agents.

Secure it
Prioritize cyber risks in real-time
Prioritize and address threats with clear, evidence-based insights to safeguard your most critical assets.

Save money
Optimize spend, boost performance
Integrate current investments under a single platform, driving cost efficiency and technology effectiveness.
Real-time visualization and reporting all in one place
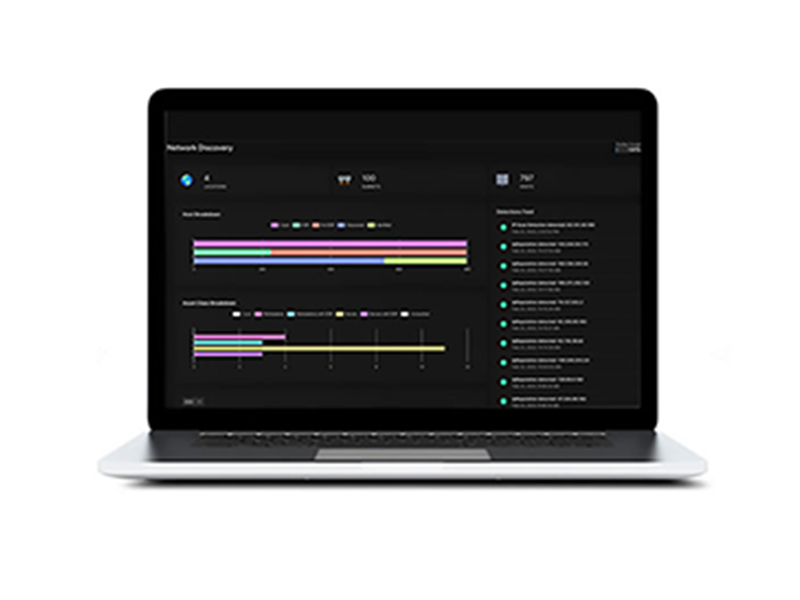
#1
Agentless Discovery of all network elements, analysis of traffic and trends, and deep dives on any specific device, app, host, iOT/OT, or cloud service.
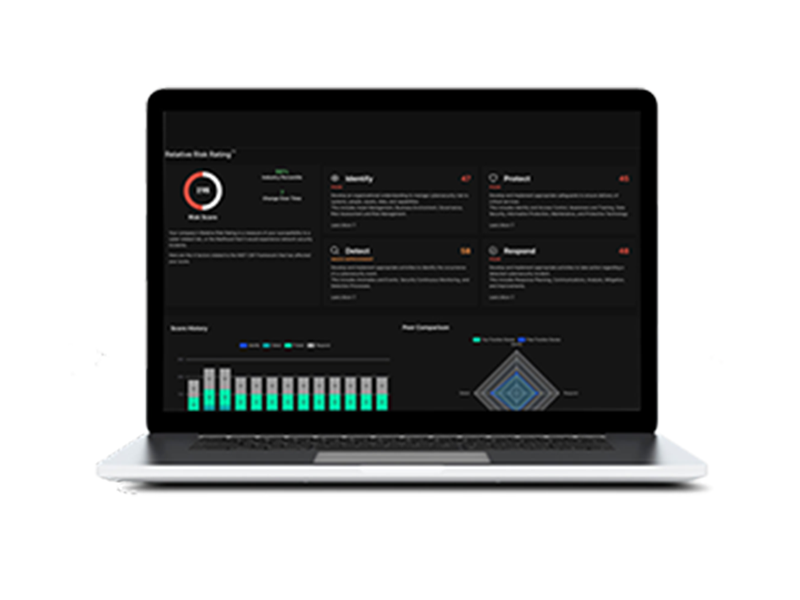
#2
Relative Risk Rating (R3) across standard NIST risk factors for your entire environment with intelligent insights on risks and resources.
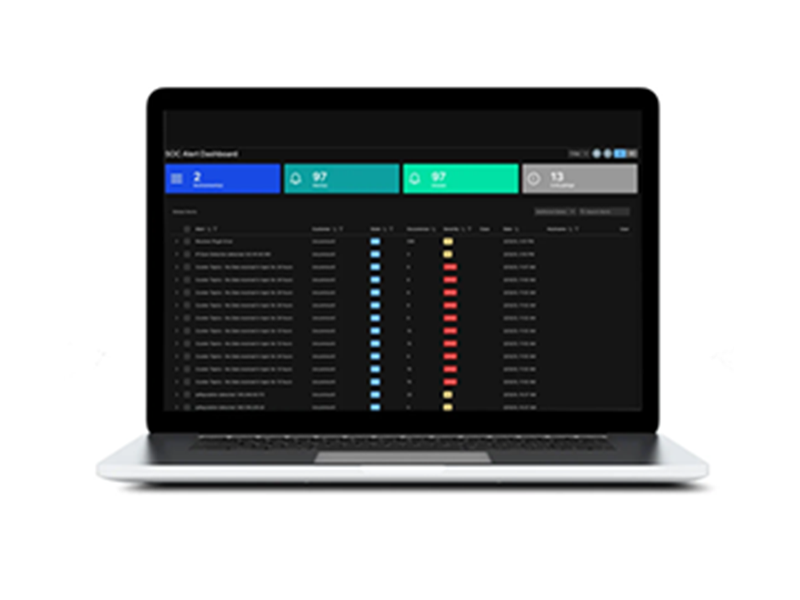
#3
Real-time alert dashboard sorts and prioritizes from all connected devices and helps investigate, contain, and remediate.
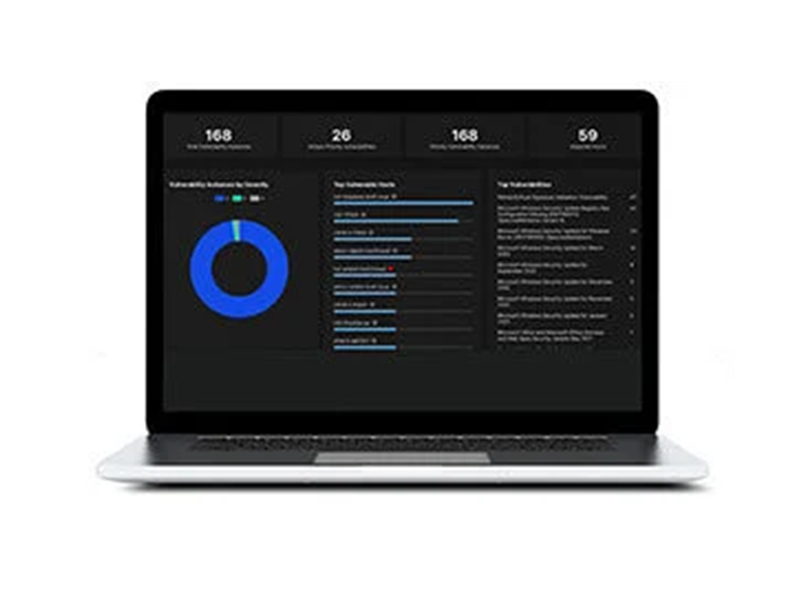
#4
Central Intelligence feature provides comprehensive assessment of vulnerabilities and enables proactive threat hunting

AI that works for you
Built-in
resilience
Smarter AI. Faster risk response.
Advanced AI continuously accelerates discovery, enhances risk insights, and streamlines response. Our patented Exposure Management platform applies AI to understand your environment in real time, using AI fingerprinting to profile every asset with greater accuracy.
Learn More About The Platform →
Risk scoring
reimagined
Stronger context. Better decisions.
AI enhances our Relative Risk Ratings (R3) and threat intelligence models by analyzing broader data sets. With intelligent recommendations and compliance-ready reporting, your team spends less time chasing alerts and more time securing what matters most.
Learn More About R3 →
Efficiency
unlocked
Spend less. Secure more.
Our application of AI provides contextual real time analysis, using system data and LLMs to provide explicit remediation actions that save time and money. Advanced detection and impactful response that sees everything, secures it, and optimizes your environment.
View Case Studies →

"We were very impressed by how quickly UncommonX was able to come in, respond to our incident, and get us back up and running safely. For those reasons, we have decided to move forward and are excited to keep working with UncommonX for 24x7x365 security monitoring of our entire IT environment."
"UncommonX provided a scalable XDR solution supported by its Exposure Management platform and 24/7 Managed SOC, streamlining the MSP’s security offerings while improving efficiency."
"UncommonX is nothing but incredible. Their Exposure Management platform and 24/7 Security Operations Center (SOC) provides continuous monitoring, which gives us peace of mind knowing that any potential threats are being addressed in real time—even after hours or on weekends."
"UncommonX is an excellent partner. UncommonX comes in alongside us and functions as an extension of our team. Every time we add anything that is possible to monitor, UncommonX immediately brings that into the collection of information to ingest, analyze, and take action if necessary. Their team is super responsive and knowledgeable. We're very happy to work with them to help us mature our security posture."
"UncommonX offers uncommonly good service and protection. UncommonX knows my corporation and me. I speak to real people on a regular basis. We also have monthly check-ins to look at our data, correct our weaknesses, and answer any questions. They offer 24/7 monitoring of our network and that gives me a great sense of peace of mind. Their dashboards integrate well with our existing equipment and software."
"UncommonX is a true partner to our IT and Security Operations. We rely on their platform to see everything in our environment, orchestrate our IT strategy, and create a more secure and resilient network."
"UncommonX was deployed really quickly, integrated all our systems together, and gave me the complete visibility I have been looking for years. We pay all this money to other companies, but none of those platforms play as well with other tools as UncommonX."
"I rely on the scale and functionality of the UncommonX Exposure Management platform to enable me to see everything on my network, manage and secure it, and operate my business more efficiently. I am extremely impressed with UncommonX’s expertise, thoroughness, and responsiveness."
"One of the most valuable aspects of UncommonX is how well the platform consolidates everything in a single view to help us understand our environment. The biggest takeaway was how quickly we could go from visibility to action."
"UncommonX offers high-end protection. They stay on top of anything security related 24/7/365. We are notified immediately of anything going on, which makes us feel safe on the work they are performing. I would recommend them one hundred percent."
Our platform
The only AI-powered platform with complete visibility

Agentless Discovery

Universal Integration

Relative Risk Ratings (R3)
AI-powered solutions
MDR/XDR
Deploys quickly and easily to map your entire network, infrastructure, and devices for a secure and optimized environment.
24/7 Managed SOC
Protects your organization from external threats and manages remediation when the unexpected happens — 24/7, 365 days a year.
Asset Discovery & Management
Know exactly what devices and systems are in place, and manage your business more effectively.
Vulnerability Management
Progressively manage your security and IT strategy, adjusting key policies based on threat intelligence.
XDR for MSPs
A scalable, licensed XDR solution for SMB and enterprise clients, powered by our patented Exposure Management Platform, providing real-time visibility, reduced costs, and optional 24/7 SOC support.
Proven, patented technology
When we say patented, we mean it. Twenty-four patents and counting. All recognized for innovations in Exposure Management and AI, providing our customers with complete visibility of their entire networks and their relative risk in real time.
.png?width=179&height=250&name=patents-badge-blue%20(1).png)
Solutions by industry
Education
Complete visibility of your school's entire network, infrastructure and devices, and their relative risk in real time.
Learn More
Financial Services
Protects banks, credit unions, insurance firms, and fintech companies from external cyber threats while managing remediation 24/7/365.
Learn More
Healthcare
Protect your network from OT, IoT, and Shadow IT risks, while managing external threats and remediation, 24/7.
Learn More
Hospitality
Protects hotels, resorts, restaurant groups, and casinos from external threats, while managing remediation 24/7/365.
Learn more
Manufacturing
Cost-effective, unified view of compliance to meet cybersecurity standards and excel in DoD contracts.
Learn More
MSPs
Reduce cost and complexity for customers by delivering an advanced cybersecurity solution that protects them 24/7/365.
Learn More
Do you have complete visibility?
Learn more about Exposure Management and how our patented platform can help your business achieve complete visibility and 24/7 protection across your entire network.
UncommonX insights
3 min read
What SICUR 2026 Revealed About OT and IoT Risk
Mar 5, 2026 by Rich Pasewark - CEO, Board Director
3 min read
How AI-Powered Reporting Turns Cyber Data into Actionable Outcomes
Mar 3, 2026 by Rich Pasewark - CEO, Board Director





